Are you a CISO or senior leader owning information security who struggles with reporting to the right person in your organization? Do you feel your voice is not heard, your recommendations are not taken seriously, or communications to the board of directors are filtered? If so, you are not alone. Many CISOs face challenges with where they report and how they communicate with their senior management.
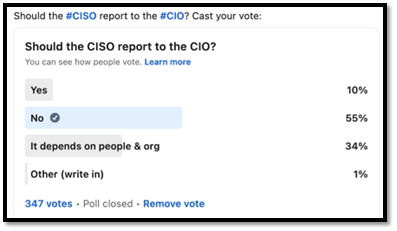
In a recent poll, with 347 votes, 55% of respondents felt that the CISO should NOT report to the CIO, 34% said that it depends on the people and organization at hand, and 10% said that the CISO should NOT report to the CIO.
Comments from contributors to the poll included several salient perspectives.
- Independence from technology ownership and competing interests (budget, cost reduction, digital transformation pressures)
- More transparent and direct communications are required to the board (without layered executive filters) regardless of where the CISO reports
- Posing the better question of “what is the conflict if this does happen and how does it get resolved?”
This question about “how do you make it better if you do happen to report to the CIO” is a critical one, as many companies still use this traditional model. So, since this reporting reality is likely to continue for many organizations, this article will give some perspectives and actionable recommendations.
Let’s first dive deeper into the current state landscape and challenges:
According to a recent ISACA study/survey, only 23% of CISOs report directly to the CEO, while 40% report to the CIO and 27% report to another executive. This can create a disconnect between the CISO and the business objectives, as well as a lack of authority and accountability for cybersecurity decisions.
Some of the common challenges that CISOs face when reporting to the wrong person are:
- Difficulty in aligning cybersecurity strategy with business goals, priorities, and risks
- Lack of visibility and influence at the board level (especially when the CISO doesn’t directly present or executives dilute the messages and transparency)
- Conflicting agendas and expectations from different stakeholders
- Limited resources and budget for cybersecurity initiatives
- Resistance or indifference to cybersecurity best practices and standards
For some companies, these pain points can be solved by changing whom the senior-most security leader reports to. However, this is likely largely dependent on the focus, engagement, and agendas of whomever the reporting structure is shifted to, as any executive could have a high or low motivational fit as well as competing priorities.
What can senior cybersecurity leaders do when stuck in a sub-optimal reporting relationship?
- Determine and demonstrate the value and impact of cybersecurity on business outcomes and reputation. Figure out whether there is a path to increasing market share, creating a competitive advantage for business, and increasing customer transparency and trust)
- Gain trust and support from the top management and other executives – this can be done by clarifying accountability outside of IT of key initiative sponsors within lines of business where human risk exists and bringing senior leaders together on a committee or
- Educate and raise awareness about cybersecurity risks and opportunities. Take out all of the techno mumbo-jumbo and have business-oriented conversations that are risk focused on the industry/market/business that your company plays in.
- Streamline collaborate and increase partnership with other functions and departments on cybersecurity matters (legal, privacy, compliance, physical security, HR, etc)
For more information on increasing the quality of communications, relationships and influence between CISOs and other executive leaders, check out “Building Senior Leader Engagement in Cybersecurity”
At Reveal Risk, we evaluate, design, and deliver strong processes and results in cyber, privacy, and risk that work efficiently, are fit-for-purpose, and are sustained. If you want assistance building your company’s cyber security strategy, governance, and plan towards desired state maturity, please don’t hesitate to contact us at info@revealrisk.com.
317.759.4453
About the Author
Aaron is a former Eli Lilly IT and security senior IT/Security/Audit/Privacy/Risk leader with over 20 years of experience in the pharmaceutical and life sciences sector. He founded the risk management working group for the H-ISAC (Healthcare Information Security and Analysis Center) which enabled information sharing and benchmarking across pharma, payers, and health care providers. Aaron is a certified Six Sigma blackbelt with career emphasis on building and improving internal processes and controls.